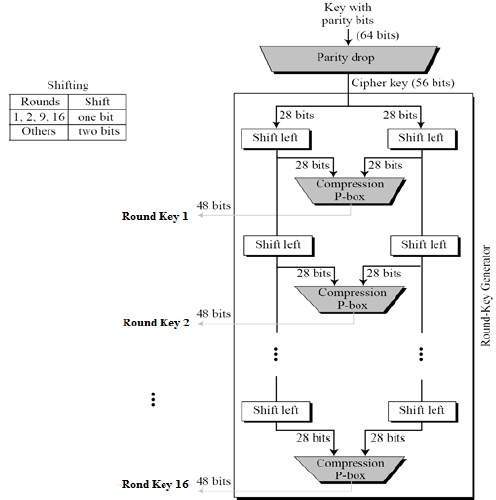
Key generation is the process of generating keys for cryptography. The key is used to encrypt and decrypt data whatever the data is being encrypted or decrypted.
Moreover my organization has many of the safety and security certs you can discover via the internet so that you have no reason to concern yourself with any type of complications. Basically run that Dragon Age: Inquisition keygen and then wait around a moment and also have fun in video game. So, what Dragon Age: Inquisition download keygen is actually doing is really joining to data store as well as get through certainly there your cd key. As to why to paid 55 dollars to purchase Dragon Age: Inquisition if you possibly can produce your personal code and then have fun with the game 100% free. Dragon age origins cd key generator.
Modern cryptographic systems include symmetric-key algorithms (such as DES and AES) and public-key algorithms (such as RSA). Symmetric-key algorithms use a single shared key; keeping data secret requires keeping this key secret. Public-key algorithms use a public key and a private key. The public key is made available to anyone (often by means of a digital certificate). A sender will encrypt data with the public key; only the holder of the private key can decrypt this data. Windows 7 professional 32 bit activation key generator free download mac.
The lecturers also use this tool for delivering the lectures to their classes.The excel worksheets widely used to make the assignment records the scientific data and the statistics. Microsoft Office 2013 Product KeyAs the product of the Company are under their copyrights, and they issue the Product key for every product. You can say the office tool becomes the central part of every profession. Microsoft office 365 product key generator 2013. There are Billions of the users all over the world who are using the office tool for managing their work in a well-defined way.
Cryptography relies upon two basic components: an algorithm (or cryptographic methodology) and a cryptographic key. This Recommendation discusses the generation of the keys to be managed and used by the approved cryptographic algorithms. The Java KeyGenerator class (javax.crypto.KeyGenerator) is used to generate symmetric encryption keys.A symmetric encryption key is a key that is used for both encryption and decryption of data, by a symmetric encryption algorithm. In this Java KeyGenerator tutorial I will show you how to generate symmetric encryption keys.
Tiberium wars screenshots. EA doesn't care for cnc anymore. Originally posted by Infinite Parabola of Ducks:So i bought this game years ago, and i wanted to play it again, i managed to find the box, the little poster, and the key commmands, but not the instructions with the key to unlock it (back in the days of cd's you had to use a code to download it) so i cannot play it, and i already bought it so i think it would be silly to buy it again, and i can get a free code, is this ok, seeing i already bought it?free codes may/may not work, and its illegeal but who cares.
Since public-key algorithms tend to be much slower than symmetric-key algorithms, modern systems such as TLS and its predecessor SSL as well as the SSH use a combination of the two in which:
- One party receives the other's public key, and encrypts a small piece of data (either a symmetric key or some data that will be used to generate it).
- The remainder of the conversation (the remaining party) uses a (typically faster) symmetric-key algorithm for encryption.
The simplest method to read encrypted data is a brute force attack–simply attempting every number, up to the maximum length of the key. Therefore, it is important to use a sufficiently long key length; longer keys take exponentially longer time to attack, making a brute force attack invisible and impractical.
Currently, commonly used key lengths are:

- 128-bits for symmetric key algorithms.
- 1024-bits for public-key algorithms.
Key generation algorithms[change | change source]
In computer cryptography keys are integers. In some cases keys are randomly generated using a random number generator (RNG) or pseudorandom number generator (PRNG), the latter being a computeralgorithm that produces data which appears random under analysis. Some types the PRNGs algorithms utilize system entropy to generate a seed data, such seeds produce better results, since this makes the initial conditions of the PRNG much more difficult for an attacker to guess.
In other situations, the key is created using a passphrase and a key generation algorithm, using a cryptographic hash function such as SHA-1.
Related pages[change | change source]
- Distributed key generation: For some protocols no party should be in the sole possession of the secret key. Rather, during distributed key generation every party obtains a share of the key. A threshold of the participating parties need to work together in order to achieve a cryptographic task, such as decrypting a message.
Cryptography Algorithms List
References[change | change source]
Key Generation Algorithms In Cryptography 2017
Microsoft office word key generator download.